Latest Gear Live Videos
Skype patches recovery password vulnerability

Posted by Jason Diaz Categories: Corporate News, Microsoft, Software,

Microsoft, the parent company of Skype, has patched a password recovery tool bug that Russian hackers utilized to exploit and gain access to user's accounts with nothing more than their account name and email. According to The Next of Web, they independently verified the five step process and confirmed that it works. Skype made this announcement on its website blog:
Early this morning we were notified of user concerns surrounding the security of the password reset feature on our website. This issue affected some users where multiple Skype accounts were registered to the same email address. We suspended the password reset feature temporarily this morning as a precaution and have made updates to the password reset process today so that it is now working properly. We are reaching out to a small number of users who may have been impacted to assist as necessary. Skype is committed to providing a safe and secure communications experience to our users and we apologize for the inconvenience.
Read More  | Skype
| Skype
Advertisement
Google pays Russian hacker $60k for bypassing Chrome’s sandbox

Posted by Andrey Malskiy Categories: Google, Internet, Mods / Hacks,
It wasn’t too long ago I was in the Eastern Block of Europe. As you would expect, I had my run in with hackers, excessive vodka drinking, and the mob. But nothing quite says "Russia," like hackers. You want free software? They got it. So it comes to us to no surprise that a Russian university student hacked Google Chrome with bypassing the sandbox.
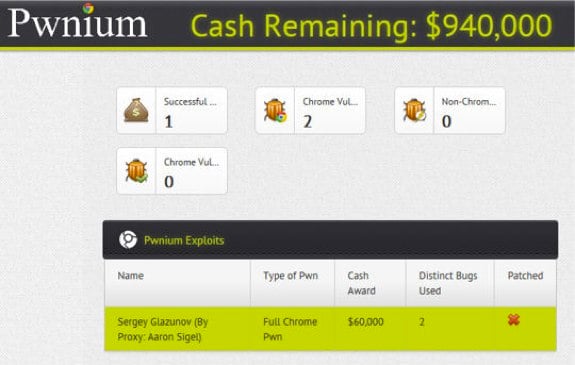
Now before you get alarmed and up your antivirus and firewalls, Google okayed this hack; more so, it was a competition put on by Google. The hack was the handy work of Sergey Glazunov, who is a regular contributor to Google’s security research department. Glazunov scored a payoff of $60,000 in Google’s new Pwnium hacker contest which began to run this year as an alternative to Pwn2Own.
According to Justin Schuh, a member of the Chrome security team, Glazunov’s by-pass was Chrome specific, which allowed him to bypass the sandbox entirely. Furthermore he added that Glazunov’s work was “very impressive” and would allow the hacker to do anything on the machine. However, bypassing the sandbox is not a trivial matter; that is why Google paid out $60,000 for the hack. A fix has already been released.
Read More  | ZDNet
| ZDNet
Sony sues PlayStation 3 fail0verflow hackers

Posted by Drea Avellan Categories: Culture, PlayStation 3, Sony,

However popular hacking or moding consoles has become, one thing remains true -- it's Illegal. A fact Sony is not willing to overlook. Sony Computer Entertainment America (SCEA ) is suing 21 year-old hacker George Hotz (AKA "geohot") and more than 100 members of fail0verflow, who contributed to the release of the PlayStation 3's root key. However, this is not new to Sony. Last year Hotz published an exploit for the PlayStation 3, but it wasn't until this year that the hackers released a complete "jailbreak" of the system. "SCEA charged Hotz and the others with violations of the Digital Millennium Copyright Act, the Computer Fraud and Abuse Act, plus breaches of California copyright law, breach of contract, and other violations. SCEA also asked the court for a temporary restraining order preventing the plaintiffs from posting any code, including the so-called Elliptic Curve Digital Signature Algorithm keys, encryption keys, dePKG firmware decrypter, or other tools." Restraining order? Ouch.
This restraining order has been set in motion to prevent Hotz to post the jail break information on this website. But we all know this never works, right?
Read More  | Games Industry
| Games Industry
Let the Apple TV hacking begin!

Posted by Andru Edwards Categories: Apple, HDTV, Home Entertainment, Mods / Hacks,
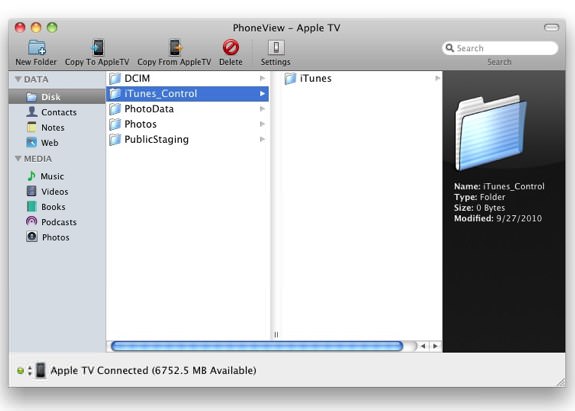
Looks like Eric Sadun over at TUAW has found that the new Apple TV is definitely hackable, as the device is instantly recognizable by PhoneView (an OS X app that let’s you browse the disk of your iOS devices.) Since the Apple TV runs iOS and has been found to pack 8GB of storage, aside from the fact that the Apple TV version os iOS has already been hacked by the iOS Dev-Team using their SHAtter jailbreak, it’s a no-brainer that we will be seeing third-party apps on this thing at some point in the very near future.
Read More  | TUAW
| TUAW
iPhone 4 unlock now available with ultrasn0w!

Posted by Andru Edwards Categories: Apple, Smartphones, Handhelds, Mods / Hacks, Software,
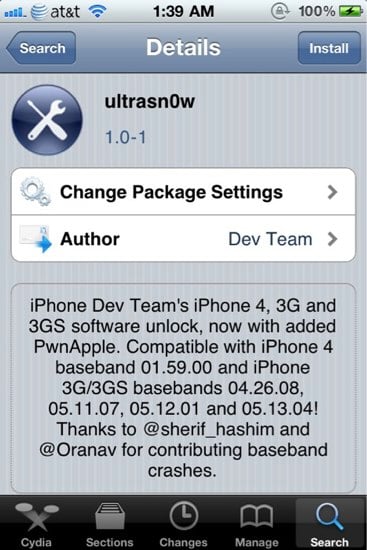
We knew that once the iPhone 4 jailbreak dropped, it would be just a matter of time before the unlock method would be made available. Well, two days later, it’s here. Ultrasn0w, the software unlock we’ve come to know and love over the years, has been updated to version 1.0-1. With that update comes support for the iPhone 4 baseband 01.59 and iPhone 3G and iPhone 3GS basebands 04.26.08, 05.12.01, and 05.13.04. If those numbers confuse you, no worries, this basically just means that any iPhone 3G/3GS/4 device that you have in your hand as of today is unlockable. Just download ultrasn0w through Cydia, and you’re all set!
Read More  | Dev-Team
| Dev-Team
Google: China Hackers Stole Valuable Source Code

Posted by Finnian Durkan Categories: Google, Internet,
 According to McAffee CTO George Kurtz the cyber-attacks that occurred in January targed a small number of employees who controlled source code management systems. These source code management systems handle the myriad changes that developers make as they write software, the breach of which can have a cascade effect across multiple levels of Google and as many as 30 other business targeted in the January attacks. Aside from being awesome and using ‘cyber-attack’ in a sentence, I also have some valuable source-code for sale at rock-bottom prices; check out my store at ‘CyberNinjaAssassinCassanova138’ on eBay.
According to McAffee CTO George Kurtz the cyber-attacks that occurred in January targed a small number of employees who controlled source code management systems. These source code management systems handle the myriad changes that developers make as they write software, the breach of which can have a cascade effect across multiple levels of Google and as many as 30 other business targeted in the January attacks. Aside from being awesome and using ‘cyber-attack’ in a sentence, I also have some valuable source-code for sale at rock-bottom prices; check out my store at ‘CyberNinjaAssassinCassanova138’ on eBay.
Read More  | ComputerUser
| ComputerUser
iPhone 3GS Unlocked and Jailbroken

Posted by Andru Edwards Categories: Apple, Smartphones, Handhelds, Mods / Hacks, Software,
 The iPhone 3GS can finally be unlocked and jailbroken. This past Friday, George Hotz released his Purplera1n iPhone 3GS jailbreak tool. Of course, once the iPhone 3GS was jailbroken, it was only a matter of time before unlocking was possible.
The iPhone 3GS can finally be unlocked and jailbroken. This past Friday, George Hotz released his Purplera1n iPhone 3GS jailbreak tool. Of course, once the iPhone 3GS was jailbroken, it was only a matter of time before unlocking was possible.
According to George:
“Normally I don’t make tools for the general public, and rather wait for the dev team to do it. But guys, whats up with waiting until 3.1? That isn’t how the game is played. We release, Apple fixes, we find new holes. It isn’t worth waiting because you might have the “last” hole in the iPhone. What last hole…this isn’t golf. I’ll find a new one next week.”
Click to continue reading iPhone 3GS Unlocked and Jailbroken
Read More  | On The iPhone
| On The iPhone
The Internet’s Riskiest Search Terms

Posted by Sheila Franklin Categories: Google, Internet,
 Using sources such as Google Zeitgeist and Yahoo 2008 Year in Review, McAfee analyzed search terms to come up with list of the 10 riskiest. Shane Keats and team analyzed over 2,600 items and say that hackers look for “crowds” at sites like MySpace or users who are about to take an online action such as downloading an MP3.
Using sources such as Google Zeitgeist and Yahoo 2008 Year in Review, McAfee analyzed search terms to come up with list of the 10 riskiest. Shane Keats and team analyzed over 2,600 items and say that hackers look for “crowds” at sites like MySpace or users who are about to take an online action such as downloading an MP3.
1. Word Unscrambler
2. Lyrics
3. MySpace
4. Free Music Downloads
5. Phelps, Weber-Gale, Jones and Lezak Wins 4x 100m Relay
6. Free Music
7. Game Cheats
8. Printable Fill in Puzzles
9. Free Ringtones
10. Solitaire
Monster Database Hacked

Posted by Sheila Franklin Categories: Corporate News, Internet, Mods / Hacks,
 Looking for a job on Monster? Then you may be at risk of security theft. Apparently their database was hacked into worldwide and data such as user IDs and passwords, email addresses, names, phone numbers and some basic demographic data was accessed. The site suggests that you change your password and has a security page with more guidelines. They do not ever contact you by email, so if you see one that looks Monster related, delete it quickly as it may be a phishing scheme. We would suggest that you never post a resume online as this is way more info than you should put out there.
Looking for a job on Monster? Then you may be at risk of security theft. Apparently their database was hacked into worldwide and data such as user IDs and passwords, email addresses, names, phone numbers and some basic demographic data was accessed. The site suggests that you change your password and has a security page with more guidelines. They do not ever contact you by email, so if you see one that looks Monster related, delete it quickly as it may be a phishing scheme. We would suggest that you never post a resume online as this is way more info than you should put out there.
Read More  | Monster
| Monster
Electronic Traffic Signs Hacked

Posted by Sheila Franklin Categories: Editorial, Mods / Hacks, Transportation,
 We were surprised when we learned that electronic road signs are easily hackable. This is because the usually locked access panel is often left unprotected. Even more surprising is that the site iHacked tells you exactly how it is done with step by step instructions. They then caution,
We were surprised when we learned that electronic road signs are easily hackable. This is because the usually locked access panel is often left unprotected. Even more surprising is that the site iHacked tells you exactly how it is done with step by step instructions. They then caution,
*** WARNING - YOU SHOULD NEVER TAMPER WITH THESE SIGNS ***
Hmm. Isn’t that a bit like posting details on how to build a bomb and then saying that it is for informational use only?
Read More  | iHacked
| iHacked
Advertisement
© Gear Live Inc. {year} – User-posted content, unless source is quoted, is licensed under a Creative Commons Public Domain License. Gear Live graphics, logos, designs, page headers, button icons, videos, articles, blogs, forums, scripts and other service names are the trademarks of Gear Live Inc.