Latest Gear Live Videos
How iPhone Thieves Can Ruin Your Digital Life in Minutes

Posted by Andru Edwards Categories: Apple, Smartphones, Videos,

Imagine this: You’re at a bar with your friends, enjoying a drink and chatting. You take out your iPhone to check something and enter your passcode. You don’t notice the person behind you who’s watching your every move and memorizing your passcode. A few minutes later, they snatch your iPhone from your hand and run away.
You might think that’s bad enough, but it gets worse. Within minutes, the thief has used your passcode to gain access to your iPhone and change your Apple ID password, which enables them to disable Find My, make purchases using Apple Pay, gain access to passwords stored in iCloud Keychain, and scan through Photos for pictures of documents that contain a Social Security number or other details that could be used for identity theft.
This is not a hypothetical scenario. It’s a real threat that has been happening across the US. The Wall Street Journal’s Joanna Stern has been hearing from victims who have lost thousands of dollars and their entire digital lives after their iPhones were stolen with the thieves obtaining their passcodes.
Click to continue reading How iPhone Thieves Can Ruin Your Digital Life in Minutes
Advertisement
Bleeding Edge TV 513: Our #DigitallyDark Giveaway Winner!

Posted by Andru Edwards Categories: Cell Phones, Features, PC / Laptop, Podcasts, Software, Videocasts, Videos,
We announce the winner of our #DigitallyDark Absolute LoJack Premium Family Pack giveaway in this episode! Did you win?
Don't forget to subscribe to Gear Live's YouTube channel--also, we are giving away awesome perks for our Patreon backers - thanks for your support!
Click to continue reading Bleeding Edge TV 513: Our #DigitallyDark Giveaway Winner!
Giveaway: Absolute LoJack Premium Family Pack

Posted by Andru Edwards Categories: Announcements, Smartphones, Features, PC / Laptop, Videos,
We've been taking part in the Absolute LoJack #DigitallyDark challenge, giving up our smartphones for a full 24 hours to emulate what it might feel like to have them stolen. As part of the campaign, we're giving away an awesome Absolute LoJack Premium Family Pack. That gives the winner give 1-year Absolute LoJack premium subscriptions, which can be installed on any Mac, PC, or Android devices they own, giving them the ultimate in protection with a guarantee that they'll get the device(s) back in the event of theft. If it isn't back in your hands in 60 days, they'll give you $1000 to help replace the laptop, and $600 for a tablet or smartphone. How cool is that?
Ready to enter? Simply use the widget below to keep track of your entries! If you're a Gear Live Patreon backer at any level, you get an extra 25 entries in this giveaway! We've got a lot of ways for you to enter even if you aren't, but don't check off any that you don't actually perform. If you do, you'll be eliminated:
Oh, and if you wanna get in on all this awesomeness, use this link to get 30% off any Absolute LoJack subscription until June 30th--just enter promo code DARK30 at checkout!
Click to continue reading Giveaway: Absolute LoJack Premium Family Pack
Apple OS X Mavericks 10.9.2 now available, here’s what’s new

Posted by Andru Edwards Categories: Apple, PC / Laptop, Software,
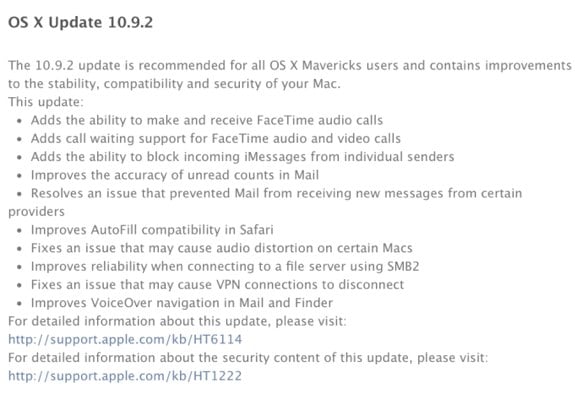
Apple has released OS X Mavericks 10.9.2 to the public following a lengthy developer beta, and with it comes quite a few new features and enhancements to the Mac desktop operating system:
- FaceTime Audio in the FaceTime and Messages apps
- Contact blocking for FaceTime and iMessage
- Mail app improvements
- Autofill fixes for Safari
- Audio fixes
- VPN fixes
- VoiceOver fixes
Also included is the SSL security vulnerability fix that Apple fixed in iOS last week, and earlier today on Apple TV. Many Mac apps were still at risk, including Safari and Mail. The company stated a few days ago that it planned to have a fix released "very soon," and four days later, this patch is included in OS X 10.9.2.
You can grab the OS X 10.9.2 update from the Mac App Store now.
Ask Andru: How to improve Touch ID and secure your iPhone

Posted by Andru Edwards Categories: Apple, Smartphones, Features, Software,

We're back for another installment of Ask Andru, where I take your burning tech questions and give you practical answers! This time, we have a two-parter as it pertains to securing your iPhone 5s (see our iPhone 5s review) and iPad, as well as making Touch ID work as well as expected. Here we go, these questions were sent in by Mike:
I have two questions,
- I have a two part question, what is the best security app for the iPad mini with Retina display & the iPhone 5s?
- Since I picked up my new iPhone 5s from the AT&T Store-Lynwood this past October and two exchanges for two new replacement phones from the Apple Store @ Alderwood Mall, the Touch ID still has not worked for me. Have other users had problems with the Touch ID? In regards to exchanging my 5s for a 5c or a Droid phone, I have been informed that it is past their respective fourteen day warranty period to facilitate an exchange because their operating systems will not allow this transaction to take place. So thus, AT&T and Apple have left me with a defective product.
Regards,
Mike
Let's start with that first one. When most people talk about security apps, I think they're asking about something that will protect them from viruses and malware getting installed on their mobile devices. For Android, for example, you might want to have something installed due to the rampant malware that can be found in the Google Play store. However, Apple sandboxes each app, and as such, none get full access to take over your device, no matter how hard they try. Apple also has a vetting process for each app as well, so there are no antivirus or anti-malware apps that you'll need. Yet, one app that I do love for security and protection is called 1Password. Let me explain.
Click to continue reading Ask Andru: How to improve Touch ID and secure your iPhone
Apple sets up Developer Center system status page

Posted by Jason Diaz Categories: Apple, Mods / Hacks,
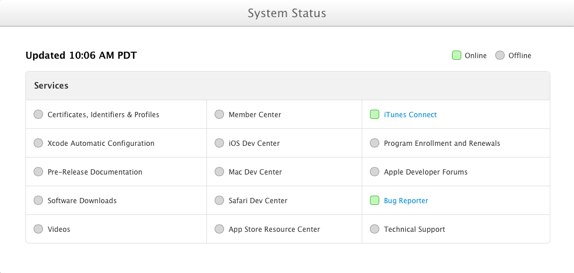
In light of last week's security breach by a security analyst, Apple has proactively introduced an online status page, much like the iCloud status page, but for the Developer Center. This status page allows registered Apple developers to track the progress as systems become available while Apple overhauls their backend services with added security. As you can observe there's still a lot of green missing. Here's a road map statement of their approach in bringing their services back online.
We plan to roll out our updated systems, starting with Certificates, Identifiers & Profiles, Apple Developer Forums, Bug Reporter, pre-release developer libraries, and videos first. Next, we will restore software downloads, so that the latest betas of iOS 7, Xcode 5, and OS X Mavericks will once again be available to program members. We'll then bring the remaining systems online. To keep you up to date on our progress, we've created a status page to display the availability of our systems. - Apple
Read More  | MacRumors
| MacRumors
Syrian Electronic Army strikes VoIP provider Viber

Posted by Jason Diaz Categories: Corporate News, Internet,

The Syrian Electronic Army strikes again at another VoIP provider, this time, Viber. We reported the cyber attacks on Tango, now it seems that the pro-Assad militant cyber group claims allegedly that it was able to download backups of Viber's database, which includes but it's not limited to phone numbers, device IDs and, supposedly, push notification tokens. Along with the purported intrusion, some Viber pages have been defaced. Viber has come forward and has stated that the intrusion is mostly harmless to customers of their VoIP services since they claim that the most vital user information is kept in a different database that can't be exploited by outsider threats. As always, Viber requests that 200,000 users be vigilant and report any suspicious activity with their accounts.
Today the Viber Support site was defaced after a Viber employee unfortunately fell victim to an email phishing attack. The phishing attack allowed access to two minor systems: a customer support panel and a support administration system. Information from one of these systems was posted on the defaced page.
It is very important to emphasize that no sensitive user data was exposed and that Viber’s databases were not “hacked”. Sensitive, private user information is kept in a secure system that cannot be accessed through this type of attack and is not part of our support system.
We take this incident very seriously and we are working right now to return the support site to full service for our users. Additionally, we want to assure all of our users that we are reviewing all of our policies to make sure that no such incident is repeated in the future. - Viber
Read More  | Arstechnica
| Arstechnica
Tango Messenger user info hacked by Syrian Electronic Army

Posted by Jason Diaz Categories: Software,

The Syrian Electronic Army (SEA) has come forward claiming that it has stolen millions of user email addresses, phone numbers and contact information of the popular video messaging service Tango. The 1.5 terabyte worth of compromised data has been confirmed by Tango on Twitter.
SEA has stated that it will hand over the information to its country's government lead by embattled President Bashir al-Assad. The compromise was possible due to an outdated WordPress installation.
Traditional telecommunication is to be avoided due to current war in Syria that has resulted in the rising death toll of over 100,000 lives. Thus, popular messaging services with VoIP capabilities are very popular in that part of world. So, it comes to no surprise that the exploit is for the sole purpose of monitoring, stamping out and finding rebel forces and sympathizers.
"Tango experienced a cyber intrusion that resulted in unauthorized access to some data. We are working on increasing our security systems. We sincerely apologize for any inconvenience this breach may have caused our members." -Tango
Read More  | Syrian Electric Army
| Syrian Electric Army
Apple Developer Portal hacked, security researcher responsible comes forward

Posted by Jason Diaz Categories: Apple, Corporate News,
The Apple Developer Center portal has been in hiatus since last Thurday. Reasons for it being down took many by surprise as they were led to be believe it was related to a mundane web maintenance. However, Apple has come forward with information that the Dev site was compromised. Now, a security researcher named Ibrahim Balic has come forward claiming responsibility for the exploit several hours before the Dev site went into full lockdown.
Balic managed to see and copy Apple developer's full names and corresponding Apple ID and emails with an unavoidable injection tool attack. No other information was garnered from the exploit such as credit card information or App codes. Such information is under additional lock and key encryption housed in other servers.
Balic claims that he was also able to get a hold of the Apple ID of regular users. He stresses that this is for security research purposes only and he does not intend to give out any information to the general public as to how he managed the exploit. Full Apple statement below. Still, no apologies from Apple over the faux linen landing page. Here's a video of Balic discribing vulnerabilities within Apple's web services.
Read More  | AllThingsD
| AllThingsD
SIM card encryption hack found in millions of mobile phones

Posted by Jason Diaz Categories: Smartphones, Mods / Hacks,

A SIM card vulnerability has been uncovered in the encryption used in millions of phones that could allow hackers to send spoof texts. These texts would execute nefarious software that enables them the ability to listen in on calls, as well as read and send text messages, all within a couple of minutes. It could even copy your SIM card.
Cryptographer Karten Nohl and his security team has estimated that 750 million phones in circulation today are using an old 56-Bit DES encryption standard used in SIM cards that can be exploited. Nohl will present his findings at the annual BlackHat security conference held in Los Vegas. It is estimated that 25% of 1000 SIM cards tested in North America and Europe were vulnerable to the exploit.
In addition, it has been reported that Nohl has fully disclosed his findings to the GSM association, and that they have notified carriers and SIM venders of who exactly can be exploited. Nohl suggested that older obsolete systems should be replaced with new triple-based DES encryption.
Read More  | PCMag
| PCMag
Advertisement
© Gear Live Inc. {year} – User-posted content, unless source is quoted, is licensed under a Creative Commons Public Domain License. Gear Live graphics, logos, designs, page headers, button icons, videos, articles, blogs, forums, scripts and other service names are the trademarks of Gear Live Inc.